The Importance of Cell Phone Detectors for Protecting Organizations
As technology continues to advance, threats to an organization’s security and intellectual property have become a significant challenge. These threats can originate from both internal and external sources, including unknown origins.
With the increasing capabilities of cell phones and tablets, these threats have become even more insidious. Perpetrators can use their devices to record targeted data and transmit it out of a facility via Wi-Fi or cellular networks. Once the transmission is complete, they can easily erase any evidence from their devices without fear of being discovered. This is why cell phone detectors have become a critical tool in protecting organizations from such threats.
The Insider Threat to Organizations and the Government
The insider threat is a significant concern for organizations, and it can be particularly worrisome for government agencies that deal with classified information. Despite significant investments in security measures, many agencies remain vulnerable to insider threats.
According to a 2013 report from the Office of the Director of National Intelligence, 44% of 39 departments and agencies, including the Defense, Justice, and Homeland Security Departments, have failed to meet the minimum standards required for an effective insider threat program. This highlights the need for increased vigilance and the use of tools such as cell phone detectors to detect and prevent unauthorized data transmission.

Organizations are sometimes even encouraging their employees to use their own cell phones for business use, which results in increasing threats to data security. Ominously, employees will link their cell phones to organization networks. The risks involved include:
Connecting to unsecured wireless networks
Downloading and installing unapproved apps
Viewing potential malicious websites
Leaving the cell phone unattended
These risks plus the accidental loss of the cell phone pose very grave threats to medium-sized business data. Rooster malware can take control of Android devices and their functions once it has been installed on a mobile device. This gives cyber criminals remote access to affected devices. Once the device is connected to it, It also grants access to the Small and Medium-Sized Business (SMB’s) network.
One very effective way of countering the danger from cell phones is to electronically monitor the environment of interest so cell phone transmissions can be detected and stopped by security. The cell phone detector technology is delineated in this article.
What is a Cell Phone Detector, Exactly?
The cell phone detector is a technological device that detects the presence of cell phones in an area or within a stipulated range of operation. Once this cell phone detector discovers the existence of a cell phone, the alert system raises the alarm and instructs the mobile phone user to switch it off. The cell phone detector has different ways of alerting the user of the phone.
It can do this by giving off a visual or voice alert in that vicinity alert message, or by silently logging all detected activity.
The operator of the cell phone detector can load a prerecorded voice message that will be played on detection of a cell phone. This is an excellent way to prevent the use of cell phones in sites of worship, examination halls, private rooms, theatres, and other sensitive areas. The employment of the cell phone detector is also one of the methods of managing cell phones in the classroom or workplace.
The cell phone detectors are usually small wall or ceiling mounted devices, but also can be portable. They can sense the presence of an activated mobile phone from a distance of just a couple of feet up to one hundred and fifty feet. The cell phone detectors can not only discover mobile devices that are in the conversation mode alone, but they can also be used for those cell phones that are in standby mode or those that are simply turned on.
Because it is not always possible to check every person entering sensitive places like libraries, worship places, or any strategic site, the use of a cell phone detector is of critical importance in these areas.. They can also be used as rescue devices.
A cell phone detector is also useful for detecting the use of mobile phones for spying and unauthorized video transmission. The illegal use of cell phones is a growing and dangerous problem in correctional institutions worldwide. They are a significant threat to prison security and circumvent the monitoring processes while assisting inmates in committing new crimes both inside and outside the facility.

How Cell Phone Detector Technology Works
As cell phone technology has advanced, so too has cell phone detector technology. These devices have been engineered to very high standards providing excellent detection accuracy with virtually zero false positives.
Signal Detection vs Signal Jamming
Cell phone detectors are able to detect an RF (Radio Frequency) transmission signal, similar to what a radio might pick up over the air. The moment the RF transmission signal from an activated cell phone is detected, the LED light starts blinking and it begins making a beeping alarm sound. This alarm continues until the mobile phone is located and turned off or until the RF transmission signal ceases. It is not suitable to use an ordinary RF detector that is employing tuned LC circuits for detecting signals present in the GHz frequency band, which are used in cell phones.
While cell phone detectors simply sense the presence of a mobile phone, a mobile phone jammer actually prevents its use – even if it is just switched on – by overpowering any network signals. Mobile phone jammers are devices that give off signals in a frequency that are in a similar range that cell phones employ, successfully obstructing the communication by creating powerful interference. When the cell phone comes within the range of the jammer, it loses its signal from the base station or cell phone tower. The cell phone will simply show “no reception strength” or “no service”.
It is important to note that while cell phone detection is legal in the United States (and many other countries), cell phone signal jamming is illegal.

When a cell phone is active, it transmits the signal in the form of a sine wave that passes through the air. The encoded audio/video signal contains electromagnetic radiation that is picked up by the receiver in the base station. The transmitter power of the modern 2G antenna in the base station is 20 to 100 watts.
The cell phone transmits short signals at regular intervals to register its availability to the most proximate base station. The most critical environmental factor is the distance to the cellular base station. Usually, the nearer a cellular phone is to a base station or transmitting tower, the weaker the signal needs to be coming from the phone.
The range of frequencies of different categories are 1) AM radio frequencies between 180 kHz and 1.6MHz, 2) FM radio frequencies between 88 to 180 MHz, and 3) television frequencies between 470 to 854MHz. Waves at higher frequencies but within the RF region are called microwaves. Cell phones employ a high-frequency RF wave in the microwave region that carries a large amount of electromagnetic energy.
Block Diagram and Working of Cell Phone Detectors
The following is a simple diagram of a simple cell phone detector. This obviously does not employ any complex circuitry that may be used in the most modern cell phone detectors that are in use today.
The circuit employs a 0.22μF disk capacitor to capture the RF signals from the cell phone. This part should function like an antenna, so the capacitor is arranged like a mini loop aerial. With this arrangement, the capacitor works like an air core with the ability to oscillate and discharge current. The output of the transistor is within 10 mV of either supply voltage terminal.
The lead inductance acts as a transmission line that intercepts the signals from the cell phone. An ordinary RF detector using tuned LC circuits is not suitable for detecting signals in the GHz frequency band used in mobile phones. That is why more complex circuitry detecting gigahertz signals is required for a cell phone detector that may be in use today, and able to detect signals from 20Mhz to 6Ghz.
Op-amp is used in the circuit to act as a comparator. It can come with MOSFET inputs and bipolar output. The input contains MOSFET transistors to provide very high input impedance and very low input current. It possesses a high speed of performance which is suitable for a low input current application. This results in a very low input current and a very high speed of performance. It is used in applications such as ground-referenced single-supply amplifiers, fast sample hold amplifiers, and long-duration timers.
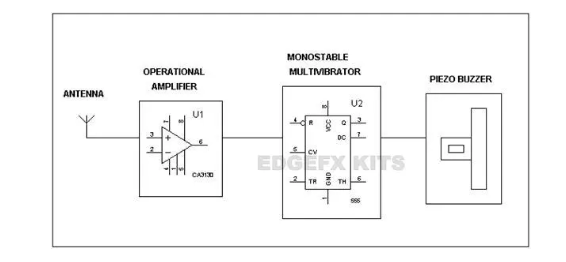
IC-555 is a very stable controller that is capable of producing accurate timing pulses. With the monostable operation, the time delay is controlled by one external resistor and one capacitor. With a stable operation, the frequency and duty cycle are accurately controlled by two external resistors and one capacitor. These are used in applications like precision timing, pulse generation, and time-delay generation.
One lead of the capacitor receives DC from the positive rail and the other lead goes to the negative input of IC1. So the capacitor receives energy for storage. This energy is applied to the inputs of IC1 so the inputs of IC1 are almost balanced with 1.4 volts. In this state, the output is zero.
However, at any time, IC can release a high output if a small current is induced to its inputs. When the cell phone radiates due to high-energy pulsations, the capacitor oscillates and releases energy.
When the mobile phone signal is detected, the output of U1 becomes high and low alternately according to the frequency of the signal. This triggers a mono-stable timer U2 through.
When the TR pin of 555timer goes low, then pin3 of the timer becomes high. When pin3 is high, the buzzer will ring.
You may use a short telescopic-type antenna. The unit will give a warning indication if someone uses a cell phone within a radius of 1.5 meters.
Again, the capabilities of this simple cell phone detector are very limited in frequency and range of detection.
Cell Phone Detector Capabilities
A top-quality cell phone detector scans for cell phones and user-selectable RF transmissions. They have become capable of detecting cell phones in all countries in standby, texts, and data and call modes. They can also discern all protocols including 2G, 3G, 4G, LTE, 5G, GSM, CDMA, Wifi, and Bluetooth enabled products, in addition to two-way radios, and even bugging devices.
These devices have a detection radius that can be easily adjusted for small rooms or for larger spaces.
Another excellent feature of cell phone detectors is that they can be coupled with software that can enable users to view alert locations on an interactive map of the facility or use the interactive graph feature to easily identify problem areas and trends.
Cell Phone Detectors in Action
Cell phone detectors provide protection from cell phones in virtually every industry. This includes:
Sensitive government and military buildings
Government SCIF’s (Sensitive compartmented information facility)
Prisons and other correctional facilities
Casinos and gaming centers
Warehousing and other retail spaces
Classrooms and examination rooms
Call centers
Intellectual property
Food production and preparation
Mines
Ports
Courtrooms
Aerospace
Manufacturing Facilities
Optimal Locations and Scenarios for Deploying Cell Phone Detectors
The Importance of Cell Phone Detectors in Sensitive Locations
Cell phone detectors are crucial for detecting cell phones and transmission devices in sensitive locations such as Sensitive Compartmented Information Facilities (SCIFs), government buildings, and embassies. A SCIF is a secure room or data center that guards against electronic surveillance and prevents data leakage of sensitive security and military information.
This is a paramount concern because modern cell phones are multi-tasking devices that can record and transmit audio, video, and other sensitive information. Their small size and advanced features make them an effective espionage tool that can be used to steal classified information. In such sensitive locations, deploying cell phone detectors is essential for protecting against potential data breaches and ensuring the security of sensitive information.

The Versatile Functions of Cell Phone Detectors
Cell phone detectors serve a variety of functions, including eliminating contraband cell phones in prisons and other correctional facilities. With a cell phone detector, prison staff can detect unauthorized phones on the premises, maintaining the security of the site and keeping inmates and personnel safe from external threats. Monitoring certain areas where contraband cell phones may be present can also provide actionable intelligence.
In addition, cell phone detectors can detect hidden transmission devices in casinos and gaming facilities. The use of cell phones and miniature cameras by cheaters has become a major concern, as these devices can transmit real-time video that gives players an unfair advantage. Cell phone detectors can locate concealed camera transmission devices and alert security staff, preventing significant financial losses for the house and other customers while protecting the integrity of table games.
Overall, cell phone detectors are a versatile tool that can be used to enhance security in a variety of settings, from correctional facilities to gaming establishments.
The Benefits of Cell Phone Detectors in Warehouses and Retail Premises
Cell phone detectors can also be useful in warehouses and retail premises, providing an additional layer of security against intruders with cell phones. If a trespasser manages to enter the premises after hours, a detector can alert security staff and prevent the theft of valuable goods.
It’s important to note that cell phone detection extends beyond the line-of-sight or perimeter of the building, making it an excellent complement to other security measures such as door and window sensors and infrared motion detectors. By using a combination of these tools, businesses can significantly enhance their security and protect against potential theft or damage to their property.

Intellectual property is another hot issue today’s global economy. A good cell phone detector can secure intellectual property (IP), techniques, and processes and prevent industrial espionage. It can assist you in guarding against covert attempts to gather intelligence about trade secrets and other classified information. This includes the physical layout of the manufacturing processes or the physical layout of research facilities. Design areas in buildings are of particular importance to avoid leaking their most valuable intellectual property.
It is also highly important to protect the integrity of exams, courseware, and testing centers. As we know, some individuals taking tests will try to cheat. In today’s environment, the cell phone is an excellent way to get information into or out of the exam room, either by text or using search engines to look up the required information.
In other cases, it may be important to prevent leakage of the details of the exam or test to protect the examining organization’s proprietary information. To do that requires detecting concealed cell phones in exam rooms and testing facilities. This will help prevent any unauthorized communication to or from the exam or test locations. For instance, to prepare and deploy some professional exams can cost hundreds of thousands of dollars.

Other critical areas where cell phone detectors can be invaluable include:
Board rooms and lawyers’ offices
Places of worship
Courtrooms
Military bases
Hospitals
Theatres
Conferences
The Crucial Significance of Cell Phone Detectors
The Importance of Cell Phone Detectors in Various Settings
Sophisticated cell phones are a potential threat in various settings, including government buildings, correctional facilities, casinos, warehouses, classrooms, call centers, and intellectual property spaces. Fortunately, technology has evolved, and cell phone detectors are now available to help mitigate these threats.
Despite the availability of these detectors, many members of the public may not be aware of their existence. This highlights the need for the media to provide information on this important technology. Cell phone detectors can detect cell phones in all countries, regardless of their operational modes, and can discover a wide variety of protocols. The most advanced detectors can even identify unknown frequencies transmissions and be programmed to detect any number of different frequencies, making them an invaluable tool in enhancing security in various settings.
Zone Protector by Cellbusters: A Comprehensive Cell Phone Detection Solution
Cellbusters is confident that our Zone Protector can address all your cell phone detection needs. This device functions like a mini spectrum analyzer, allowing users to scan frequency ranges as defined by them.
The Zone Protector can alert, notify, control third-party devices, or simply log any related transmission activity as soon as it’s detected. Its capabilities go beyond traditional cell phone detectors as it continuously scans the environment for any cell phones and user-selectable RF transmissions. The user can adjust the detection radius to suit smaller or larger spaces, providing complete control over the device’s range. With its comprehensive features, the Zone Protector is an excellent solution for enhancing security in various settings.
Zone Manager by Cellbusters: A Powerful Tool for Cell Phone Detection
Cellbusters’ Zone Manager is another valuable product that can display visual alerts on an interactive map in your facility when a cell phone is detected. It can monitor multiple cell phone detectors simultaneously, providing complete oversight of your entire facility.
At Cellbusters, we are committed to providing 100% comprehensive support to our customers and answering any questions they may have. With our focus solely on cell phone detection, we have been industry leaders since 1999, providing cutting-edge solutions to enhance security in various settings.