Signal jammers are a real threat in the present times, and not just limited to movies. Do you know what signal jammers are, and how can you protect yourself from signal jamming attacks?

While signal jamming may seem like something straight out of a spy movie or a tool for state censorship, it is also a possible attack from a neighbor or a hacker.
The modus operandi of signal jamming can be incredibly isolating, causing the victims to lose access to the internet or even regular phone service. The attack can also be challenging to combat. However, if you encounter a signal jamming attack, there are several measures you can take to tackle it.

Understanding Signal Jamming – Causes and Effects
Signal jamming refers to the deliberate disruption of wireless connections between devices and their access points. This disruption causes a type of Denial of Service (DoS) attack, leading to devices in the vicinity losing access to the internet while the jamming is in progress.
The intentions behind signal jamming may vary from reasons related to privacy, such as when a company or an individual wants to prevent the use of internet-enabled devices on their premises, to state censorship and cyberattacks.
How Does Signal Jamming Work?

Devices on a wireless network send and receive information using data packets at a specific frequency. Signal jamming involves using a jammer to send “noise” that disrupts the frequency band on which wireless devices operate.
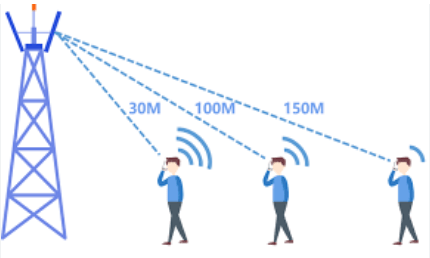
A signal jammer can be a hand-held, portable device that prevents wireless communications within a 15-meter radius. Portable jammers can be purchased or self-made. These jammers are relatively cheap, disrupt communication on specific frequencies, and are mostly used for personal privacy and security reasons

Conversely, stationary jammers are made to be installed in a building or mounted on a platform. Stationary jammers can affect a wider area and disrupt wireless communications on a broad range of frequencies, including blocking drones. These features make stationary jammers more expensive, energy-demanding, and, thus, suitable for enterprise purposes.
Is Signal Jamming Legal?
No. Individual possession and use of signal jammers in the United States is illegal, per Sections 302(b) and 333 of the Communications Act of 1934. This law prevents individuals, businesses, and even local law enforcement from using jammers. Federal law enforcement agencies are permitted under specific circumstances but must obtain judicial approval first.
The main reason for this prohibition is that signal jamming can endanger public safety, regardless of the intent. Besides personal communication, signal jamming can also interfere with emergency services.
Tampering with wireless communication is a federal offense, as per the Communication Act. Anyone who sells, buys, or uses a signal jammer in the US faces criminal and civil liabilities. But the threat of penalties has never stopped cybercriminals, has it?

What Can You Do Against Signal Jamming?
The tricky part about signal jamming is that it is difficult to detect as everything else appears to be working correctly. Although your cell phone may have reception, and your router may show no signs of malfunctioning, the jammer disrupts wireless transmission between devices and their access points, causing you to lose access to the internet.
If you suspect that you may be a victim of signal jamming, there are a few steps you can take. First, try resetting your router or turning off your phone and then turning it back on. If you still cannot access the internet, try moving to a different area as signal jamming is usually localized. In severe cases, you may need to contact your internet service provider or the authorities. Additionally, taking preventive measures such as using signal jammers to block unauthorized signals or upgrading your router’s firmware can help protect you from potential jamming attacks.
Change Your Location
Odds are, the signal jammer is one with a five to 15 meter jamming radius. So, consider moving from where you are if you can. This way, you can even meet other people and ask if their internet connection is active.
Change Your Wi-Fi Frequency
You will find instructions on how to change your router’s broadcasting frequency in the device manual. But odds are you tossed this manual away a long time ago. In that case, you will need to log in to the admin dashboard of your router and check the Wi-Fi settings.
The two frequency bands used for wireless connections are 2.4 GHz and 5.0 GHz, with most modern devices supporting both bands. Most portable jammers disrupt connections operating on the 2.4 GHz band. Changing your WiFi frequency to 5.0 GHz would help you avoid the DoS attack on the 2.4 GHz band.
However, there is a con: the 5.0 GHz band supports higher speeds but has a shorter range. You would need to be closer to the router as the signal cannot easily penetrate solid objects like walls. Although effective at avoiding the DoS attack, the range restriction makes changing your Wi-Fi frequency a temporary measure.
Change Your Wi-Fi Frequency Channel

This measure is a long shot compared to changing your Wi-Fi frequency entirely. However, it’s worth a try, especially if your device does not support higher frequencies.
Devices that broadcast on the 2.4 GHz frequency have 11 to 13 channels, with each separated by about 5 MHz. On the other hand, the 5.0 GHz frequency has 25 channels, each separated by at least 20 MHz and up to 160 MHz.
Switching channels is a tricky thing to do, especially on the 2.4 GHz frequency. You want to avoid interference from overlapping channels. The small channel width on the 2.4 GHz frequency makes interference from overlapping channels very likely. Conversely, the wider channel widths on the 5.0 GHz frequency mean you’re less likely to have this problem.

Detecting and Eliminating Signal Jammers.
If all other methods fail to restore your disrupted wireless connection, a possible solution is to locate and remove the signal jammer. However, this method may prove difficult as signal jammers can be easily concealed, especially the portable, palm-size models.
Despite the challenge, attempting to find and remove the jammer is still worth a try. Since jammers have a limited range of around 15 meters, the attacker would most likely be nearby. Look for a radio-like device with an antenna, which could be the signal jammer. However, if the jammer is inside a backpack or a neighboring private property, your chances of locating it would decrease.
It is also unlikely for attackers to use stationary jammers with wider ranges as it could disrupt more people and public infrastructure, which could attract unwanted attention from law enforcers. Nonetheless, it is important to remain vigilant and take preventive measures to protect your wireless network from future attacks.
Call Your Service Provider

If you are having trouble accessing the internet, it may be due to a problem with your Internet Service Provider (ISP). There are various reasons why your ISP may have disconnected your service or caused downtime. For instance, it could be due to unpaid bills or a violation of their Terms of Service. Additionally, service downtime may occur due to upgrade processes, faulty equipment, or unfavorable weather conditions.
To determine whether your ISP is responsible for the disruption in your connection, it is advisable to contact them directly. Confirm with them if your account is still active, and if they are experiencing any service disruption in your area. In most cases, ISPs can resolve such issues by resetting your account or carrying out necessary repairs.
Taking proactive measures such as regularly paying your bills, reporting faults promptly, and backing up important data can help minimize the impact of such disruptions on your online activities.
It Could Be Something Else Besides Signal Jamming
Signal jamming is a less common type of DoS attack because federal law prevents the manufacture, import, and sale of jammers in the United States. So, your inability to access the internet could be the result of other types of DoS attacks like a disassociation attack.
What Are Disassociation Attacks?
This tactic can mean your data ends up in the hands of cybercriminals. So what is a disassociation attack and how can you protect yourself?

Imagine you’re cruising on an open road when a truck blocks the main road. The blockade forces you to take a detour through a one-way street, where people in an unmarked van seize and strip you of your valuables.
That is essentially how a Wi-Fi disassociation attack works: the road is your internet connection, your car is your router, the people in the van are hackers, and your valuables are data stored on your phone. So how does a disassociation attack work? How can you protect yourself?
What Is a Disassociation Attack?
A disassociation attack is a cyberattack where a hacker forces a device to lose internet connectivity either temporarily or for an extended time. One second, you’re using your internet, and the next, your connection vanishes.
Your phone or laptop will try to reconnect as usual, but your router will be unavailable. The attack can be one where the attacker simply wants to kick you off the network for fun. However, it is seldom so. Most disassociation attacks are by hackers who want a profit.
And usually, in that case, when your device attempts to reconnect to the router, it’ll be connecting to an evil twin (cloned) router the attacker has set up for that purpose. Most people won’t notice a difference when they connect to a cloned router, but their internet activities will be visible to the attacker.
How Does a Disassociation Attack Work?
Disassociation attacks are a form of cyber attack that occurs when hackers exploit security loopholes or vulnerabilities in a network’s setup. These loopholes may be inherent in the protocol of the technology used for Wi-Fi connections. For example, some protocols may have inherent weaknesses that attackers can exploit.
Alternatively, disassociation attacks may be carried out when a target uses an unsecured Wi-Fi network or a protocol with weak security. In this scenario, the attacker can gain unauthorized access to the network and carry out the attack.
Regardless of the cause, it is essential to take steps to secure your network against disassociation attacks. This may involve using secure protocols, regularly updating firmware and software, and implementing strong authentication mechanisms. By being proactive and taking necessary precautions, you can protect yourself against this type of cyber attack.
Hacker Finds the Router and Connected Devices
In an area with high internet traffic, an attacker would need to identify the router to attack, as well as the devices connected to it. They typically do this using network sniffing tools.
Network sniffing tools are mostly software—but sometimes hardware—that monitors network traffic. These are freely available on the internet for consumer and business use. Company admins typically use these tools to monitor customer bandwidth usage. For example, it’s how a café would know you’ve exhausted your free 1GB allowance or that your 30-minute access to free Wi-Fi is up.
Hackers, however, use network sniffers to get the information they can use to launch an attack. Generally, they’re looking for information about the origin and destination of data packets and the security/encryption protocol used. More specifically, they also want to know your device’s MAC address, IP addresses, Wi-Fi 802.11 standard, and the Wi-Fi security protocol (WEP or WPA).

Hacker Initiates a Denial of Service (DoS) Attack

Armed with the aforementioned information, the hacker may then launch their disassociation attack via a MAC-level Denial of Service (DoS). Here, the hacker sends a barrage of deauthentication packets to capture your router’s management frames.
This attack will cause the connected device to disconnect. Then, when the device tries to reconnect, the attacker can exploit the steps in the Wi-Fi reauthentication protocol to perform a brute-force attack on the password. Hacking this password gives the hacker access to your internet activities.
Alternatively, a hacker may clone your router and boost the clone’s signal strength. When your device searches for available networks, it will see and connect to the spoofed router instead of the original router. In this case, your internet activities will also be in full view to the hacker.
How to Protect Yourself From Disassociation Attacks
You cannot prevent a hacker from targeting you with disassociation attacks. However, you can protect the privacy of your internet activity, keep files on your computer secure, and even bat off the attacks with the right setup.

Secure Your Wi-Fi
For starters, you should enable your Wi-Fi security and use a strong password. Your Wi-Fi password should be at least 16 characters long and comprise of alphanumeric characters.
Also, most routers and internet-enabled devices come with default Wi-Fi passwords. A web search can provide a hacker with this information. So, as a rule of thumb, you should always change default passwords on your devices.
Spoof Your MAC Address
It’s not fun to do, but consider spoofing your MAC address. Spoofing your MAC address is not an absolute guarantee, but it will make it even harder for a hacker to level a disassociation attack against you. Perhaps even hard enough for the hacker to give up.
There are two ways to spoof a MAC address on Linux: for beginners and power users. Meanwhile, the process of spoofing a MAC address on Windows is much easier to follow. Likewise, the process isn’t complicated on macOS devices either.
Use a VPN
A VPN encrypts the content of your internet traffic, so anyone snooping cannot see it. You can think of the way a VPN works as driving through a tunnel to avoid a helicopter. Although a VPN cannot prevent a disassociation attack, it can conceal the contents of your data packets from hackers on the network.
Use Antivirus Software

In addition to securing your Wi-Fi and using a VPN, also consider using antivirus and keeping the virus definitions up to date. Windows comes with a default protection software, Windows Defender, and it’s good enough to protect you from most threats. MacOS computers have a native defender too.
For starters, you should consider activating this layer of protection, even if you would prefer to use a third-party antivirus. This way, you get protection against malware that a hacker may attempt to install on your system.
Encrypt Your Computer
Wi-Fi security can be cracked. A VPN isn’t infallible, and an antivirus doesn’t guarantee absolute protection either. So you should also consider encrypting your device.
This way, your files will be useless to a hacker who hijacks your computer and steal your files. Setting up military-grade encryption on your Windows computer is quite easy, and the entire process can take from a few minutes to a couple of hours, depending on how much disk space you need to encrypt.
Use a Router That Supports Secure Wi-Fi Standards

802.11w is a Wi-Fi standard designed with enhanced security for management frames. Routers equipped with this standard are resilient to disassociation attacks.
Although this protocol exists, few consumer hardware support the Wi-Fi standard. Instead, consider using a router with 802.11ax (aka Wi-Fi 6), as those have better security without sacrificing backward compatibility with devices that use older standards.
Get a Wireless Intrusion Prevention System (WIPS)
WIPS are effective at preventing disassociation attacks, but they are expensive to install and maintain—making them out of reach for the individual. If you’d still rather get a WIPS, consider products like Cisco Adaptive Wireless IPS, Aruba RFProtect, and AirTight WIPS.
Switch to Ethernet
Although it may be less convenient than wireless connections, using Ethernet is an effective last resort measure to prevent disassociation attacks. Ethernet is a more secure option because it does not have the vulnerabilities and security loopholes inherent in wireless connections. However, setting up an Ethernet connection requires a lot of cables, and you will need to keep them organized and neat.
Despite the inconvenience, Ethernet is a worthwhile investment if you want to improve the security of your network. By implementing an Ethernet connection alongside other security measures, you can ensure that your network is well-protected against cyber attacks.
A hacker would have to attach a physical device to the network to carry out an attack, which means they would have to enter your home or office. Doing this would likely leave a trail of evidence and increase the hacker’s chances of being caught. Most hackers would rather find easier targets than risk getting caught.
Disassociation Attacks: A Serious Threat to Network Security.
Whether you’re at home or in a hotel, losing internet connectivity can be an unpleasant experience. Disassociation attacks can cause this problem, and most people may not realize that they are being targeted. These attacks are challenging to detect and prevent, but it is possible to minimize their impact or emerge unharmed.
During a disassociation attack, the Wi-Fi network appears to malfunction, and users may assume it is a network glitch. However, by taking proactive measures, such as monitoring network activity and implementing robust security measures, you can reduce the likelihood of being affected by a disassociation attack.
Awareness and prevention are key to defending against disassociation attacks. By understanding the potential threat and taking steps to secure your network, you can minimize the risk of being targeted and ensure that your internet connection remains stable and secure.
Understanding the 7 Stages of Hacking.
Discovering Targets and Techniques: How Hackers Identify and Attack Systems to Steal Data.

In order to fight hackers, you need to know how they operate. What do they actually do?
Most hacks follow the Lockheed Martin Cyber Kill Chain, an intelligence framework developed to identify and prevent cyberattacks. The process begins with getting information about a potential target and ends with stealing valuable data. So what are the stages cybercriminals go through when hacking a system?
The Lockheed Martin Cyber Kill Chain
Although there are variations to the process, hackers typically follow the Lockheed Martin Cyber Kill Chain in their quest to find who to hack and to carry out an attack. The Kill Chain comprises of seven steps.
1. Hackers Research and Harvest Information
The first step in a cyberattack is reconnaissance—or scoping out the target. This typically involves collecting publicly available information about a potential target, including email addresses, social media usernames, and public records.
They may get this information from data leaks or by doing the grunt work if they are interested in a specific person. In the latter case, they may resort to more sophisticated methods like a Bluetooth attack or intercepting the network, also called a Man-in-the-Middle (MITM) attack. While the former requires the hacker to be in close proximity to the target, the latter can be done remotely using software or on-site by intercepting the victim’s Wi-Fi.
The ultimate goal is to learn as much as possible about the targets, the devices they use, the devices’ operating systems, and the services they use, among other things. The information they get here can help them find vulnerabilities.
2. Hackers Find the Tools Needed to Carry Out Attacks
This stage is called “weaponization” in the Cyber Kill Chain. Armed with information about their potential targets, hackers assemble the tools they’ll need for the cyberattack. They may, for instance, create and hide malware in files that their target is likely to download.
You may think of this stage as going fishing. The gear you’ll need to pack for fishing in a freshwater lake would be different from the gear you’ll need for fishing out in the ocean. You would probably go with a different boat too.
3. Hackers Cast Their Net or Bait

This stage is called “delivery” in the Kill Chain. This step involves tricking the target into downloading the malware—basically inviting the bad guys into the fortress.
One common way hackers do this is by sending emails containing malicious files. The delivery method may also be images hosting the malware, as seen when hackers exploited the James Webb telescope images to spread malware. SQL injection is another common way hackers deliver malware.
In any way, the goal is to get the target to download malware onto their device. The malware takes over from here: automatically extracting itself and injecting it into the system.
4. Malware Exploits a Vulnerability in the System
The malware takes over once it’s on the target’s computer. Certain background actions, like USB or Media Autoplay, can trigger the malware to automatically extract and run on the victim’s device. This stage is called “exploitation”.
5. Malware Does What It’s Programmed to Do
This phase in the Kill Chain is called “installation”. Once the malware gets into the system (or computer network), it silently installs in the background, usually without the victim’s knowledge. Then, it begins to scan for vulnerabilities in the system that will grant the hacker higher admin privileges.
The malware also establishes a Command-and-Control System with the hacker. This system lets the hacker receive regular status updates on how the hack is progressing. To put it into perspective, imagine the Command-and-Control System as a high-ranking military officer who’s actually a spy. The spy’s position puts them in a place to access sensitive military secrets. This status also makes them primed to collect and send stolen intelligence without suspicion.
6. Hackers’ Spy System Takes Over and Expands

The malware at this stage does several things to establish its Command-and-Control System, also eponymous for the sixth stage in the Kill Chain. Typically, it continues to scan the system for vulnerabilities. It can also create backdoors hackers may use to enter the system if the victim discovers the entry point.
In addition, the system also looks for other devices connected to the compromised devices and infects those too. It’s like when everyone at the office catches the common cold. If enough time passes, no one remembers who exactly started it.
7. Plunder, Destroy, Get Out
The final stage in the actual hacking process involves the cybercriminal using their elevated control of the victim’s device to steal sensitive data like login details, credit card information, or files containing business secrets. A hacker may also destroy the files on the system, which is especially dangerous if the victim has no backup for data that was stolen and destroyed.
The Aftermath of a Cyber Attack: What Comes Next?

The Aftermath of a Hack: Responses from Victims and Hackers.
Following a stealthy cyber attack, victims may be unaware of the breach, leaving the hacker with a constant stream of sensitive information. However, if victims do discover the attack, they may take steps to remove the malware, close backdoors and destroy any compromised devices to prevent further access by the hacker.
Organizations may also take measures to neutralize the effects of a hack, such as deactivating compromised credit cards or implementing new security measures. Meanwhile, successful hackers can reap rewards from their actions, such as holding the victim to ransom or selling the stolen data to other cybercriminals on the dark web.
Overall, the aftermath of a cyber attack can be highly damaging for victims and profitable for hackers. It is crucial for organizations to put in place effective measures to prevent such attacks from occurring and to be prepared to respond promptly and effectively if they do occur.

Preventing Hacking Attempts: How to Protect Your Systems.
Hackers use various methods to identify potential victims, ranging from simple and passive techniques to sophisticated and active ones. While this may seem alarming, you can take steps to protect yourself by practicing safe online behavior, limiting the personal information you share and leveraging cybersecurity tools such as VPNs and anti-malware software.
By adopting best practices such as creating strong passwords, regularly updating software, and being cautious of suspicious emails or messages, you can greatly reduce the likelihood of falling victim to a cyber attack. Additionally, tools like firewalls and encryption can add layers of protection to your system and data.
While no one can completely eliminate the risk of a hacking attempt, taking these precautions and utilizing modern cybersecurity tools can help you prevent and mitigate the impact of an attack.
What Are the Risks of Remote Computer Access?
More individuals and companies are using remote access programs, but they do come with security risks. So what can you do to protect yourself?

Remote computer access has many benefits. From increased productivity to cost savings, there are plenty of reasons why you, as an individual or business owner, should consider using this technology. However, there are also some risks that you need to consider before making the switch.
So what are the risks associated with remote computer access? And how can you mitigate them?
What Is Remote Computer Access?
Remote Computer Access is simply the ability to connect to another computer or network from a remote location. It allows you to use a device without physically handling it. The technology is popularly used for providing tech support and quick fixes to software problems.

You might have experienced remote access while getting technical troubleshooting on your own computer. The technician could see your screen and control your mouse and keyboard to resolve the issue.
Other than that, Remote Computer Access technology has helped a lot of businesses during the Covid-19 pandemic as employees were able to access office computers by safely remaining in their homes. It has also proved to be a cost-effective solution as it eliminates the need for traveling and accommodation expenses.
How Does a Remote Computer Access Work?
Before knowing the risks associated with using remote access, it is vital to understand how it works.
Remote Computer Access usually works by using a client-server model. For remote access to work, you need three things: a remote access client, a remote access server, and a network connection between them.

The host computer, which is the server, stores all the files and applications that the user needs. On the other hand, the client is a program that allows the user to connect to the server and use its resources. The client program is installed on the user’s computer, and they can use it to connect to the server from anywhere in the world.
Once the connection is established, the user can access all the files and applications stored on the server. They can also perform several tasks, such as creating and editing documents, sending and receiving emails, troubleshooting problems, and much more.
Risks Associated With Remote Computer Access
So you know the benefits of remote access. What are its drawbacks?
Security Breaches
One of the biggest risks associated with remote access is security breaches. When you allow remote access to your computer, you are also giving the person on the other end complete control of your system. This means they can access all your files, applications, and data. If the person is not someone you trust, they could use this information for malicious purposes, such as stealing your identity or selling your confidential data on the dark web.

Apart from that, if you are accessing your office device from your personal PC through remote access and your PC has a weak security setup, there is a possibility that the hacker could gain access to your work system as well. This could lead to a lot of damage, such as leaked confidential information, stolen data, and even financial loss.
Malware Attacks
Another major threat associated with remote access is the possibility of malware being installed on your system. If the person on the other side has malicious intent, they could install malware on your computer without you even knowing. This malware can then be used to collect your personal information or damage your system.
Other than that, most remote computer access programs do not scan the involved devices for malware. So, suppose you are remotely accessing the office computer with your malware-infected personal PC. In that case, you can inadvertently infect your office computer, as well as all the devices connect to it through a network, with malware.

Data Loss
Data loss is another concern during remote access. If there is data exchange going on and the connection between the client and server is interrupted, it could result in data being lost. This is especially critical if you are working on important files or projects. Data loss can also occur if the remote access program crashes or if there is a power outage.
Performance Issues
Lastly, another risk associated with remote access is performance issues. If the connection between the client and server isn’t strong enough, it can result in a laggy and slow experience. This can be frustrating, especially if you are working on time-sensitive tasks.

