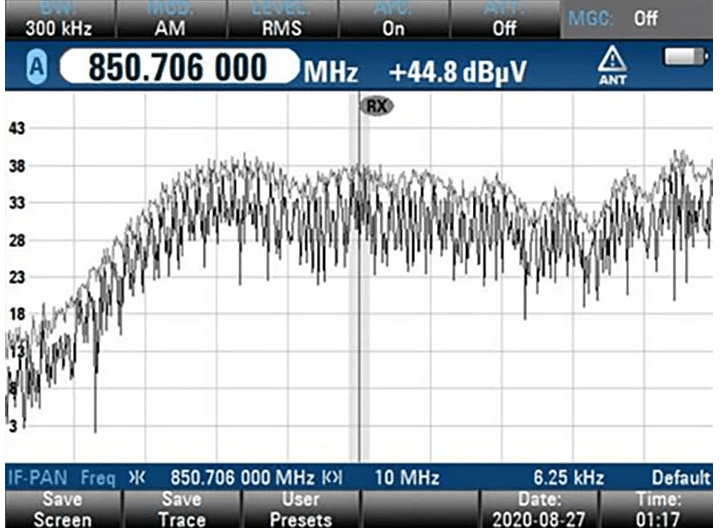
FCC Fines Company for Using Signal Jammer to Prohibit Employee Phone Use at Work
It is interesting to note the contrasting decisions made by the NLRB and the FCC regarding employee phone use at work. While the NLRB saw a policy prohibiting phone use as necessary for safety and security reasons, the FCC viewed the use of a signal jamming device as a violation of federal law. This … Read more