Can Signal Jammers Block Cameras?
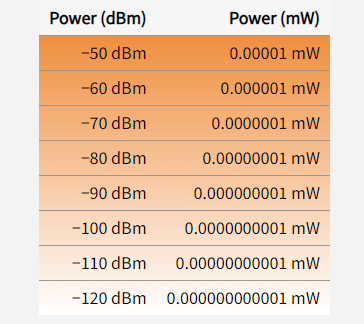
At A1 Security Cameras, we are committed to continuously educating ourselves on the challenges associated with our products. Unfortunately, as security camera technology advances, so do the methods for bypassing them, such as the use of signal jammers. These devices are specifically designed to disable or exploit wireless signals from devices such as cellular … Read more