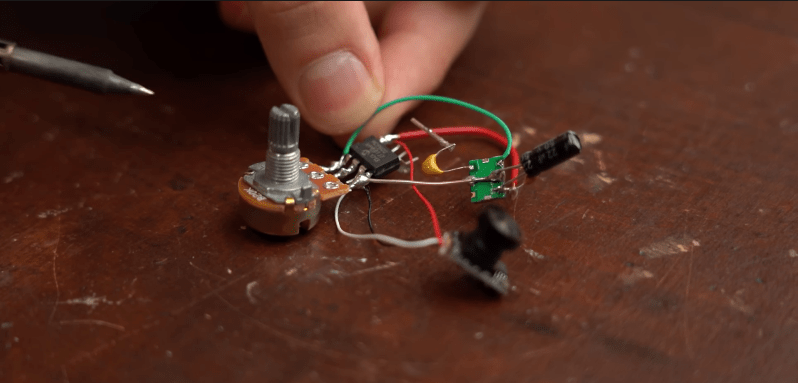
WiFi Jammer Created from DIY Video Transmitter
With the rise in popularity of FPV drones, there has been an influx of affordable wireless video technology flooding the market. Inspired by his experience of flying and crashing a cheap FPV drone, [GreatScott] decided to take on the challenge of building his own video transmitter. Little did he know, the task proved … Read more