To safeguard against government surveillance of protester phone activity, a recommended approach is to use the secure messaging app Signal and implement a PIN code for the SIM card on the phone. By utilizing Signal’s end-to-end encryption, messages and calls exchanged through the app will be protected from interception. Adding a PIN code to the SIM card on the phone can also enhance security, as it ensures that only the authorized user can access the device and its information.

According to a recent report by Ken Klippenstein in The Nation, federal agents from the Department of Homeland Security and the Justice Department deployed a highly advanced cell phone cloning technique to intercept protesters’ phone communications during the Portland demonstrations earlier this year. This revelation not only raises concerns about the government’s potential violation of constitutional rights but also begs the question: how can ordinary citizens protect their privacy and freedom of assembly in the face of such threats? Despite the alarming nature of this situation, there are various tools and strategies that individuals can leverage to safeguard their digital privacy, including encryption software and secure messaging apps. Additionally, advocating for legal protections and limitations on government surveillance practices is crucial for defending our fundamental rights.
Yes, they do. Here are two simple things you can do to help mitigate this type of threat:
As much as possible, and especially in the context of activism, use an encrypted messaging app like Signal — and get everyone you work with to use it too — to protect your SMS text messages, texting groups, and voice and video calls.
Prevent other people from using your SIM card by setting a SIM PIN on your phone. There are instructions on how to do this below.
The Mechanism Behind SIM Cloning
It is unclear from the limited information available what type of surveillance was employed by federal agents to intercept protesters’ phone communications in Portland. However, The Nation’s reference to “cell phone cloning” suggests the possible use of a SIM cloning attack. This tactic involves replicating the subscriber identity module (SIM) of a targeted cellphone. The SIM is a tiny chip used by almost all mobile devices to connect to its owner’s phone number and account, making it a valuable tool for tracking and intercepting phone communications.
Here’s how SIM cloning would work:
First, the feds would need physical access to their target’s phone; for example, they could arrest their target at a protest, temporarily confiscating their phone.
Then they would pop out the SIM card from the phone, a process designed to be easy, since end users often have reasons to replace the card (such as traveling abroad and needing a local SIM card to access the local cellular network, or when switching cellular providers).
The feds would then copy their target’s SIM card data onto a blank SIM card (this presents some challenges, as I explain below), and then put the original SIM card back without their target knowing.
The secret encryption key contained in SIM cards is used to secure the communication between mobile devices and cell towers. While the SIM card is designed to use the encryption key for communication purposes only, it is still possible to extract the key through cracking. Earlier SIM cards used a weaker encryption algorithm which made them easy to crack, but newer SIM cards have integrated stronger encryption and may take much longer to crack. It is possible that federal agencies possess a method to quickly extract encryption keys from SIM cards, which could explain why the details of the surveillance in Portland remain classified. However, it’s also plausible that “cell phone cloning” refers to something other than SIM cloning, such as extracting files directly from the phone rather than accessing SIM card data.

In the event that federal agents were able to extract the encryption key from their target’s SIM card, they could potentially return the phone to their target and spy on all SMS text messages and voice calls going forward. This would require physical proximity to their target and the monitoring of radio waves for traffic between the target’s phone and a cell tower. The key stolen from the SIM card could then be used to decrypt this traffic, which is in line with what anonymous former intelligence officials described as a “Low Level Voice Intercept” operation involving audio surveillance through radio wave monitoring.
If you were arrested in Portland and are concerned that federal agents may have cloned your SIM card while you were in custody, it would be advisable to replace your SIM card as a precautionary measure.
Taking Control of a Phone Number: A Temporary Scenario
Even if law enforcement agencies don’t clone a target’s SIM card, they could gather quite a bit of information after temporarily confiscating the target’s phone.
They could power off the phone, pop out the SIM card, put it in a separate phone, and then power that phone on. If someone sends the target an SMS message (or texts a group that the target is in), the feds’ phone would receive that message instead of the target’s phone. And if someone called the target’s phone number, the feds’ phone would ring instead. They could also hack their target’s online accounts, so long as those accounts support resetting the password using a phone number.
But, in order to remain stealthy, they would need to power off their phone, put the SIM card back in their target’s phone, and power that phone on again before before returning it, which would restore the original phone’s access to the target’s phone number, and the feds would lose access.
Making the Switch to Encrypted Messaging Apps: Why SMS is No Longer Enough
Protecting yourself from SIM cloning attacks and eavesdropping by stingrays requires moving away from SMS and traditional phone calls, which have never been secure. Instead, opt for end-to-end encrypted messaging apps like Signal, which is user-friendly and designed to disclose minimal user information. With Signal, you can securely send text messages, make voice and video calls, and participate in group chats, even across Android and iPhone platforms. To further enhance your privacy, you can use Wire or Keybase, which offer usernames instead of phone numbers as identification. Check out our detailed guide to secure messaging with Signal.
If you use an iPhone and want to securely talk to other iPhone users, the built-in Messages and FaceTime apps are also encrypted. WhatsApp texts and calls are encrypted too. Though keep in mind that if you use Messages or WhatsApp, your phone may be configured to save unencrypted backups of your text messages to the cloud where law enforcement could access them.
You can’t use an encrypted messaging app all by yourself, so it’s important to get all of your friends and fellow activists to use the same app. The more people you can get to use an encrypted messaging app instead of insecure SMS and voice calls, the better privacy everyone has. (For example, I use Signal to text with my parents, and you should too.)
None of these encrypted messaging apps send data over insecure SMS messages or voice calls, so SIM cloning and stingrays can’t spy on them. Instead they send end-to-end encrypted data over the internet. This also means that the companies that run these services can’t hand over your message history to the cops even if they want to; police would instead need to extract those messages directly from a phone that sent or received them.
Another important consideration is preventing cops from copying messages directly off your phone. To prevent this, make sure your phone is locked with a strong passcode and avoid biometrics (unlocking your phone with your face or fingerprint) — or at least disable biometrics on your phone before you go to a protest. You also might consider bringing a cheap burner phone to a protest and leaving your main phone at home.
Lock Your SIM Card With a PIN
Another way to protect against certain forms of mobile phone spying is to lock your SIM card by setting a four- to eight-digit passcode known as a SIM PIN. Each time your phone reboots, you’ll need to enter this PIN if you want SMS, voice calls, and mobile data to work.
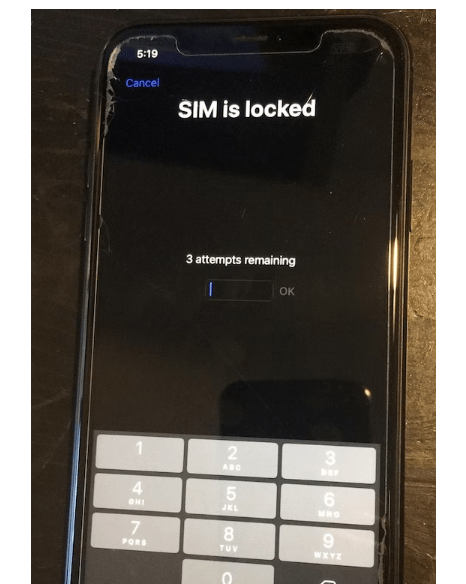
If you type the wrong PIN three times, your SIM card will get blocked, and you’ll need to call your phone carrier to receive a Personal Unblocking Key (PUK) to unblock it. If you enter the wrong PUK eight times, the SIM card will permanently disable itself.
With a locked SIM, you’ll still be able to use apps and Wi-Fi but not mobile data or cellphone service. So make sure that you securely record your SIM PIN somewhere safe, such as a password manager like Bitwarden, 1Password, or LastPass, and never try to guess it if you can’t remember it. (You can always click “Cancel” to get into your phone without unlocking your SIM card. From there, open a password manager app to look up your PIN, and then reboot your phone again to enter it correctly. I’ve done this numerous times myself just to be sure.)
If you want to lock your SIM card, first you’ll need to know the default SIM PIN for your cellphone company. For AT&T, Verizon, and Google Fi, it’s 1111; for T-Mobile, Sprint, and Metro, it’s 1234. If you use a different phone carrier, you should be able to search the internet to find it. (I would avoid guessing — if you type the wrong default PIN three times, your SIM card will get blocked.)
After discovering your default PIN, you can change it to a new one to secure your SIM card. If you have an iPhone, head to Settings, then Cellular, then SIM PIN, and set your preferred PIN. For Android phones, navigate to Settings, then Security, then “SIM Card Lock,” and enter your new PIN. If your phone model doesn’t feature the above settings, you can search the internet for specific instructions. With this method, if law enforcement gains physical access to your phone, they won’t be able to access your locked SIM card without your PIN. Furthermore, if they fail to guess your PIN correctly three times, the SIM card will block itself, requiring the PUK from your cellphone company to unlock it. If they exceed the maximum number of PUK attempts, the SIM card will permanently disable itself, making it impossible for anyone to use it.
