While the CIA may have the capability to access your phone, newly released documents indicate that they lack the ability to intercept encrypted chats before they reach their intended recipient.
Numerous news outlets have repeated a misleading claim regarding the latest release of CIA documents by WikiLeaks, suggesting that the agency has “bypassed” the encryption used by secure-chat apps like Signal and WhatsApp. While these reports imply that the CIA can circumvent the security measures of these systems, they fail to clarify that the agency’s actual capability is to take over the entire phone, which then grants access to the encrypted chats, among other things. Even WikiLeaks’ analysis of the documents acknowledges this, stating that the CIA’s techniques permit them to hack the “smart” phones running apps like WhatsApp, Signal, Telegram, Wiebo, Confide, and Cloackman, and collect audio and message traffic before encryption is applied. Nevertheless, this claim has been separated from its context by some widely-read publications, such as the New York Times.
the Boston Globe:
Mashable:
and this AP reporter retweeted by the AP itself:
Contrary to the clear implication from these journalists and news sources, the documents WikiLeaks published do not appear to show any attack specific to Signal or WhatsApp, but rather a means of hijacking your entire phone, which would of course “bypass” encrypted chat apps because it thwarts virtually all other security systems on the device, granting total remote access to the CIA.
The WikiLeaks dump also includes information about CIA malware that can hack, and remotely spy on and control, computers running Windows, macOS, and Linux. Which means that it’s also true that the CIA can bypass PGP email encryption on your computer. And the CIA can bypass your VPN. And the CIA can see everything you’re doing in Tor Browser. All of these things can be inferred by the documents, but that doesn’t mean using PGP, VPNs, or Tor Browser isn’t safe. Basically, if the CIA can hack a device and gain full control of it — whether it’s a smartphone, a laptop, or a TV with a microphone — it can spy on everything that happens on that device. Saying Signal is bypassed because the CIA has control of the entire device Signal is installed on is akin to saying the diary you keep in your bedside table is vulnerable because the CIA has the ability to break into your house. It’s true, technically, but not exactly a revelation, and odd to fixate on to the exclusion of other vulnerable items.
While the New York Times deserves credit for deleting its misleading tweet and revising its article language, there may still be some negative consequences. Many people may be left with the mistaken impression that using Signal or WhatsApp could put them at risk, when, in fact, the opposite is true. Despite the CIA’s ability to take over phones and access encrypted chats, Signal and WhatsApp still provide a high level of protection against surveillance and hacking. This incorrect interpretation of the news could have a lingering impact on the public’s perception of these apps.
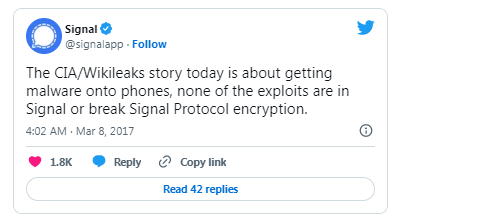
While it cannot be ruled out that the CIA has successfully cracked the encryption used by Signal, WhatsApp, or other software, there is no evidence to suggest this in the documents released by WikiLeaks today. It’s important to note that the possibility of encryption being broken always exists, but as of now, there is no indication that the CIA has accomplished this.